� February 2006 | Main | April 2006 �
March 29, 2006
Supermax lockup for spammer Rizler
 Former employees and business associates of Minnesota spam king Christopher William Smith ("Rizler") can breathe a little easier. Authorities confirmed today that Smith, 26, has been moved to a super-maximum security prison, following his indictment last week for allegedly trying to take out a hit on a witness in his federal case.
Former employees and business associates of Minnesota spam king Christopher William Smith ("Rizler") can breathe a little easier. Authorities confirmed today that Smith, 26, has been moved to a super-maximum security prison, following his indictment last week for allegedly trying to take out a hit on a witness in his federal case.
 Smith (shown here in an undated drivers license photo) is now locked up at the Oak Park Heights (OPH) facility in Stillwater, one of a handful of super maximum ("supermax") security prisons in the USA.
Smith (shown here in an undated drivers license photo) is now locked up at the Oak Park Heights (OPH) facility in Stillwater, one of a handful of super maximum ("supermax") security prisons in the USA.
OPH houses "some of America's most dangerous prisoners," according to the publisher of a 2004 book, The Big House, which describes life inside the OPH correctional facility.
Authorities said Smith is likely to remain at OPH until his trial, which is scheduled for October. A number of former employees and business associates are expected to testify against Smith, who is accused of running an illegal online pharmacy.
Although Smith is now under the same roof as violent, "worst of the worse" offenders, authorities said he is unlikely to have any dealings with them. OPH was designed to minimize prisoner contact with other humans, including prison staff. Inmates at OPH are reportedly only allowed out of their cells for one hour per day, unless they agree to participate in a job or education program.
Following Smith's attempt at witness tampering during his earlier stay at the Sherburne County Jail in Elk River, authorities at Oak Park Heights aren't taking any chances. A note in his prison file warns guards to be wary and states that Smith is "sophisticated," especially regarding medications.
 Prison life may already be taking a toll on Rizler, who's been jailed since August, 2005. According to sources in Minneapolis, Smith earned the nickname "Crybaby" as a result of some emotional moments while at Sherburne County Jail.
Prison life may already be taking a toll on Rizler, who's been jailed since August, 2005. According to sources in Minneapolis, Smith earned the nickname "Crybaby" as a result of some emotional moments while at Sherburne County Jail.
Smith's assignment to the big house is tinged with irony, according to insiders who say Smith ran Xpress Pharmacy Direct, his illegal drug business in Burnsville, almost as if it were a prison. Employees were required to pass through metal detectors on their way in and out of the building, and were prohibited from using cell phones while in the office. Surveillance cameras kept an eye on employees in the building's hallways. At one point, Smith even discussed installing cell-phone jamming technology to prevent unauthorized employee communications.
Besides an extended stay in prison, Smith is also facing a large financial judgment from America Online. Last January, Smith was ordered to pay AOL $5.6 million for spamming its members in 2003.
Smith's incarceration at a supermax prison is the latest example of harsh legal repercussions against spammers. In April 2005, Jeremy Jaynes was sentenced to nine years in prison. The conviction is currently under appeal. This past January, a court ordered an obscure spammer to pay $11.2 billion in damages to a small Iowa ISP.
Posted by Brian at 9:02 PM | Comments (11)
March 28, 2006
Spam Conference 2006 video is online
Streaming video of the 2006 Spam Conference, held today at MIT in Cambridge, Massachusetts, is now available on the web. (Requires RealPlayer version 8.) The morning session video is here, with the afternoon session here. The conference agenda can help orient you. ZDNet has a summary of some of the proceedings.
Due to a schedule conflict, I wasn't able to attend this year. Anyone care to post a mini-review?
Posted by Brian at 11:16 PM
March 22, 2006
US Attorney says Rizler threatened to kill witness
 Just when it seemed his case couldn't get any weirder, new charges have been filed against spam king and online drugstore operator Christopher Smith, aka "Rizler."
Just when it seemed his case couldn't get any weirder, new charges have been filed against spam king and online drugstore operator Christopher Smith, aka "Rizler."
According to a WCCO-TV report out of Minnesota, Smith was indicted yesterday for threatening to kill a prosecution witness in his upcoming trial over illegally operating an online drug store and other charges.
Seems Smith phoned a friend from Sherburne County Jail earlier this month and allegedly discussed plans to intimidate a witness and even have the witness or his/her family killed, to prevent the witness from testifying against him.
Apparently Smith didn't know the jail was monitoring and recording all calls made by Smith to numbers not linked with his defense attorney.
At his arraignment today, Smith pleaded not guilty.
In a press release today, the U.S. Attorney's office didn't specify which witness was targeted by Rizler. Check out some of the comments from former employees at the bottom of this earlier posting about the case, and you'll see there's plenty of animosity to go around.
Conspiring to tamper with a witness and endeavoring to obstruct justice both can draw penalties of up to twenty years, according to a report by the AP.
Smith has been jailed since last September, when he violated the terms of his release.
Smith had previously pleaded not guilty to charges including conspiracy to distribute controlled substances, wire fraud, selling misbranded drugs and money laundering.
Posted by Brian at 11:19 PM
Spamware vendor integrates anti-spam service
 Send-Safe, a notorious developer of spamming software, has updated its program to include a remove-list feature from the controversial Blue Security anti-spam service.
Send-Safe, a notorious developer of spamming software, has updated its program to include a remove-list feature from the controversial Blue Security anti-spam service.
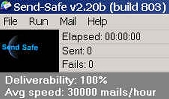
The latest build (803) of the Send-Safe Mailer v2.20b includes an option designed to prevent spammers from sending messages to any of the 245,000-plus e-mail addresses registered with the Blue Security "Do Not Intrude" registry.
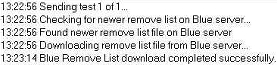
The feature, which can be accessed from the program's Advanced tab, is turned off by default. When enabled, the feature automatically kicks in each time a spammer fires off a spam run. Send-Safe Mailer appears to check to see that it has the latest copy of the encrypted Blue Security remove list. If necessary, it downloads an updated version and checks it against the spammer's mailing list. (Shown below is a brief snippet of a log file produced when I tested the feature.)
 Send-Safe apparently integrated Blue's technology using a software development kit (SDK) offered by Blue Security at its web site.
Send-Safe apparently integrated Blue's technology using a software development kit (SDK) offered by Blue Security at its web site.
The integration of Blue Security's remove lists into Send-Safe might not be optimal yet. When I tried sending myself a test spam at an address protected by Blue Security, the Send-Safe program didn't alert me or otherwise notify me that the address was in the remove list. Then again, the email address didn't appear in the program's log of successfully sent message IDs, nor did I ever receive the test message.
So far, Send-Safe hasn't made a lot of noise about integrating the Blue Security remove list. The Send-Safe User's Guide contains only this brief explanation of the new feature: "Use Blue Security Remove List: Use this to avoid sending mails to the antis on Blue Security's Remove List."
But Blue Security is happily crowing about the news. On the company's blog today, CEO Eran Reshef said, "This remarkable and inspiring event we have witnessed displays the power of our community. Many `experts' claimed spammers will never leave our members alone and we know we will prove them wrong."
![]() My take: the integration into Send-Safe could indeed be a big break for users of the free Blue Security service. Many spammers I've talked to seem put off by the complexity of manually downloading and using the service's remove-list tools. Send-Safe now makes that task totally automated. If other big spamware developers (Dark Mailer, Nexus, etc.) figure out a way to integrate the Blue remove lists, life will get even better for Blue members.
My take: the integration into Send-Safe could indeed be a big break for users of the free Blue Security service. Many spammers I've talked to seem put off by the complexity of manually downloading and using the service's remove-list tools. Send-Safe now makes that task totally automated. If other big spamware developers (Dark Mailer, Nexus, etc.) figure out a way to integrate the Blue remove lists, life will get even better for Blue members.
Prior to this development, Blue Security was seen by many spammers as purely antagonistic, since the service is designed to post complaints in the order forms of sites advertised in spams received by Blue Security members. Now, Send-Safe has given Blue a stamp of legitimacy from the spam world.
On the other hand, I doubt this integration will do much to improve Blue Security's standing among some leading anti-spammers. The whole notion of remove lists is anathema to ardent supporters of opt-in email. Blue Security, they might argue, is ultimately just providing a free list-washing service to spammers.
Posted by Brian at 2:35 PM | Comments (2)
March 19, 2006
Spammers hitch a free ride on car site
![]() I recently received a spam on my America Online account advertising "Super H0T Se11ing Quality Meds." To my surprise, the hyperlink in the message appeared to lead to Autotrader.com.
I recently received a spam on my America Online account advertising "Super H0T Se11ing Quality Meds." To my surprise, the hyperlink in the message appeared to lead to Autotrader.com.
AutoTrader.com is an Atlanta, Georgia-based company that calls itself "the internet's leading auto classifieds marketplace." Its investors include the venture capital firm Kleiner Perkins Caufield & Byers.
Was the used car site branching out into Viagra and Xanax? Nah. A closer look revealed that some clever spammer had just figured out a way to bypass AOL's URL blocklist.
When you're a spammer for a well known drug site, it can be pretty hard to get your messages past such blocklists, which contain the addresses of known "spammy" websites. Emails containing links to any of the listed URLs can cause spam filters to shunt emails off to the spam folder. But not if the URL is cleverly camoflaged.
The URL in the meds spam looked something like this (I've added line wraps):
http://adserving.autotrader.com/event.ng/
Type=click&FlightID=202867&AdID=318547
&TargetID=
Following the "TargetID" was a series of characters containing the URL of the spammed web site, but scrambled using Base-64 encoding. As a result, the spammy part of the address was "invisible" to AOL's filters (and to most users). Yet each time someone clicked on the link, the Autotrader.com site would automatically re-direct the surfer to the web address encoded in the URL -- in this case, a drug store called Comfort RX.
 There's a legitimate use for the re-direct feature at the Autotrader.com home page. The site sports a bunch of banner ads, which, if clicked, send you to the advertisers' sites (while a ca-ching sounds in AutoTrader.com's accounts receivable department).
There's a legitimate use for the re-direct feature at the Autotrader.com home page. The site sports a bunch of banner ads, which, if clicked, send you to the advertisers' sites (while a ca-ching sounds in AutoTrader.com's accounts receivable department).
There's at least one other re-direct at the site, but I haven't seen any evidence of spammers abusing it. Unless admins have gotten around to fixing it, clicking the link below should demonstrate how that URL will flip you to FBI.gov:
http://autotrader.com/redirect/redirector_link.jsp?to_url=http://www.fbi.gov
This isn't the first time spammers have exploited such open re-directs at mainstream sites. Last year, pill spammers worked a similar vulnerability at ZDNet.com.
I imagine some spammers have a script that scours the Internet looking for sites with open re-directors. Others probably just use Google. Either way, re-directs are just another item in the devious spam king's bag of tricks.
Posted by Brian at 10:02 PM | Comments (2)
March 18, 2006
US spam king confirms move to New Zealand
Television New Zealand's "One News" program has obtained an on-camera interview with Brendan Battles, in which he admitted to being the American spam king who had apparently retired last year. 
Rumors of the Florida spammer's relocation started last October, when someone anonymously posted a report of Battles' move to Kiwiland to the Nanae newsgroup.
If Battles had planned to turn over a new leaf in New Zealand, those hopes began to unravel when he made the mistake of spamming a New Zealand-based anti-spammer (sample here) earlier this month. The message was part of a small spam run advertising broadband wireless from Wired Country Direct, a unit of Compass Communications.
Following the March 3 spam incident, Computerworld published a story this week in which Battles, who now resides in Auckland, denied he was the same person reviled by anti-spammers.
Battles, who regularly tangled online with anti-spammers in the past, has returned to the Nanae newsgroup. Yesterday he blamed participants for getting him fired from Compass, where he worked as a territory sales manager.
"Well, done making me look bad, what an effort on your part. Happy that I lost my job? Well hopefully I can find something better," he wrote.
Let's hope that by "something better" he means a position that doesn't involve spamming.
Posted by Brian at 12:08 PM
March 16, 2006
On the trail of a spammer turned loan shark
Almost a year ago, I received a juicy anonymous email tip regarding a piece I wrote about George Merwin (aka George Merwyn). As you may recall, Merwin is the Florida Viagra spammer who eluded Microsoft's lawyers for years, before getting nailed last year.
 The tipster informed me that Merwin had branched out from pill spamming and now is into online loan sharking. The source claimed the lucrative business enabled Merwin to purchase "a $400,000 Ferrari, over 20 houses, including precontruction houses, a $150,000 Porsche, a 7 series BMW, a 60 foot boat, a multi million dollar home, a business jet, and the list goes on."
The tipster informed me that Merwin had branched out from pill spamming and now is into online loan sharking. The source claimed the lucrative business enabled Merwin to purchase "a $400,000 Ferrari, over 20 houses, including precontruction houses, a $150,000 Porsche, a 7 series BMW, a 60 foot boat, a multi million dollar home, a business jet, and the list goes on."
At the time, a Boca Raton paper had just published an article noting that Merwin lived in a $2.5M home at 777 Marine Drive, along with his current wife, whom neighbors identified as Rachel. 
That house in the tony Blue Inlet subdivision, it turns out, is a key bit of corroboration that Merwin may indeed have moved into Internet credit services. But I never would have connected the dots if it weren't for Sean E. Brooks.
Recently, I blogged that Brooks (aka m3rk) was believed by spammers to have acted as a confidential informant for the U.S. Secret Service. Rumors swirled last month that Brooks snitched on the recently arrested "g00dfellas" spammers Adam Vitale and Todd Moeller.
While researching Brooks, I noticed that he once listed his address as 10939 Bal Harbor Drive in Boca Raton. A check of Palm Beach County property records shows that Debora (Brooks) Merwin and George (Anthony) Merwin were co-owners of the five bedroom home at that address until 2003.
Lots of possible Peyton Place scenarios seem possible here. (George married Debora, who had a son, Sean, by a previous marriage. George introduced Sean to the world of spam entrepreneurship. George and Debora were later divorced and George married Rachel. Etc.)
After mulling over these possibilities, I belatedly got around to checking the property records for the Merwin's palace at 777 Marine. Turns out the deed actually belongs to a Chantilly, Virginia company called Tres Hombres LLC, which bought the house in January 2005 from a Kathy (Merwin) Devivo.
Why would an alleged multimillionaire like Merwin be living in a house owned by someone else -- unless perhaps George is one of the hombres?
Tres Hombres LLC is run by a Lonnie D. Gaddy III, who is also chief operating officer for a financial services company in Virginia called Universal Debit & Credit (UDCC), with Carlos Gavidia as CEO/President.
 Tres Hombres and UDCC share the same 3901 Centerview Drive address in Chantilly as several other firms -- all apparently connected to Gaddy. The firms include Quick Process, LLC and Prove-It Partners, LLC, which provide "no turndown" credit cards as well as short-term loans, and an apparently defunct merchant fraud protection service.
Tres Hombres and UDCC share the same 3901 Centerview Drive address in Chantilly as several other firms -- all apparently connected to Gaddy. The firms include Quick Process, LLC and Prove-It Partners, LLC, which provide "no turndown" credit cards as well as short-term loans, and an apparently defunct merchant fraud protection service.
Ding ding ding.
I realize there's usually less than six degrees of separation between any two spammers. That's especially true when you're dealing with bulk emailers in Boca Raton, Florida, the spam capital of the USA.
But who would have expected such a close connection between a kid rumored to be a confidential informant in a spam case, and an elusive Internet drugstore king turned loan shark?
Posted by Brian at 4:32 PM
March 10, 2006
Florida spammer linked to lost "iBill" data
Open letter to Florida spammer Glen Mccausland:
Dear Glen, are you missing several gigs of data?
Lance James of Secure Science Corporation tells me that the files he recently found containing millions of customer records were named 1ibill.rar, 2ibill.rar, 3ibill.rar and 4ibill.rar. Naturally, Lance was under the impression that the data might have belonged to iBill, Inc.
The only Google hits I could find on those filenames were from a time in 2004 when you, Glen, were apparently looking for some programming help to import some files with those same names into a SQL database. ("We own the server so you will have full access," you wrote.)
You didn't put your real name on that GetaCoder site, but you used your nickname, Pre111. You've used that nick for years, even back when you had a Prodigy account in 1997. At SpecialHam.com, you used the member ID Pre111, but listed your real name as "Glen Mac."
You even used Pre111 in the URL of your no-prescription medz site, PharmMall, which you officially announced last year.
Glen, what's the deal? Could it be that online-marketers.net, the site where you sell mailing lists, was hacked? Or did that programmer you hired to import the data make off with a copy?
Was it really iBill data or not?
Posted by Brian at 5:09 PM
Stolen "iBill" data still online
This week, Wired News published a story about a massive security lapse apparently affecting data owned by iBill, the payment processor for many porn sites. But a follow-up article published yesterday reports that the cache of 17-million-plus records may not belong to iBill after all.
iBill officials say a cross-reference of email addresses in the cache, discovered on the Internet by security firms, shows that only three are iBill customers. 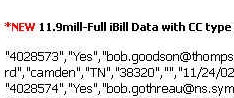
So who hemorrhaged all the customer data, if it's not iBill?
If authorities really want to find out, they can start by contacting a spam data-broker known as James Botkin.
As I reported last year, Botkin's company, then known as Optin Supply, Inc., has been offering huge databases for sale to spammers. Among the lists for sale by Botkin last year was one containing 11.9 million records described as "Full iBill Data with CC type."
A sample of the alleged iBill database offered by Botkin is still online, thanks to Archive.org. (Screen grab here.) Among the 1,048 sample records are a couple on people holding what are identified as "Dinner" cards. Presumably this means Diner's Club cards. If so, all of the nearly 12 million iBill records marketed by Botkin may not be from iBill either, since the payment company has told Wired News it doesn't accept Diner's Club cards.
So where do list brokers like Botkin get all this data? Many are apparently cutting deals with e-commerce sites and internet marketing firms for what they call "opt in" data. As I reported in my article last year, the records usually include home addresses, phone numbers, and an IP address corresponding to each list entry as evidence that the customer data was voluntarily provided by visitors to an online store or other web site.
Botkin continues to operates several sites, including onebedroomapartm.com and optinsearchdb.com, from which he sells huge collections of data. Botkin does most of his marketing via the SpecialHam.com spammers forum, where he currently uses the username bigmailmanbig.
Last month, someone started a new thread at SpecialHam.com with the subject "onebedroomapartm.com's list is BAD !!," to which forum regulars chimed in with comments like, "I cant belive you fell for this guy is data is complete usless garbage always has been always will be.. For years everyone has known it."
We may never know where the data reported on by Wired News came from. But my guess is that the big cache may simply be "opt in" data -- perhaps even from the same source that serves James Botkin.
Posted by Brian at 10:39 AM | Comments (2)
March 9, 2006
Porn-spam mom's plea
Turns out the porn-spam mom isn't a mom after all. MommyJobs.com operator Jennifer Clason has posted a detailed entry at her site about her stint in the porn-spam business. One of her "come clean" revelations: she doesn't actually have any children. 
The web posting essentially confirms the key details of Clason's recent plea agreement(PDF file). E.g., she managed porn websites from 1999 -2003 for James R. Schaffer, who operated a company called Diamond International. Schaffer also partnered with Jeffrey Kilbride. In January of 2004, Clason learned how to use a spam program capable of sending spam from a remote server in Amsterdam. Starting in April 2004, she sent millions of spams that included embedded pornographic images and used falsified "from" lines. AOL received over 600,000 complaints about the spams from January-June, 2004. Clason was paid around $30,000 for her work. Etc.
Clason even admits at her site to having taken "2 different anti-depressants to cope with this stress." (As a condition of her release in September 2005, Clason was ordered to refrain from using any alcohol, and ordered to receive alcohol counselling, as well as mental health treatment.)
What Clason doesn't address in her web posting is that, while she may have given up spamming, she's still in the porn business. As we pointed out yesterday, Clason still runs a number of porn gateway sites, including Hardcore-skank-porn.com, Broadbandblowjobs.com, and trailertrashvideos.com.
Clason also continues to recommend that her site visitors participate in a variety of dubious money-making programs, including high-yield investment programs. Clason even posted a graphic showing how much she made in one day via HYIPs, despite warnings from the Securities and Exchange Comission.
In a recent post about the conviction of a person for running a Ponzi scheme, Clason had this to say: "The stupid government should just stay out of our affairs. People know the risks, let them lose their money at their own discretion!!!"
Clason's former employer Schaffer has pleaded not guilty to all counts. His trial is set for May 2 in Phoenix. Kilbride's trial is scheduled for June 6.
Much of Clason's 16-page plea agreement is devoted to describing the requirements of her cooperation with prosecutors. Her June sentencing may be postponed, according to the document, "until such time as defendant's cooperation has been completed."
Posted by Brian at 2:31 PM | Comments (11)
Kintera, Cuban, and Common Cause
 Michael over at Spamroll noticed that dot-com celeb Mark Cuban is complaining about being spammed by Common Cause, the nonpartisan public interest group.
Michael over at Spamroll noticed that dot-com celeb Mark Cuban is complaining about being spammed by Common Cause, the nonpartisan public interest group.
Michael suspects that Cuban's been joe-jobbed because of his stand on the AOL "email tax" issue, which Common Cause has staunchly opposed.
To test this thesis, I decided to sign up for CauseNet, the group's email newsletter. I discovered that Kintera, the company that's managing the CauseNet newsletter, does a horrible job of handling confirmation.
When you sign up for CauseNet, you get a confirmation email from Kintera thanking you. (Here's what mine looked llike.) But it's not exactly closed-loop opt in (aka double opt-in), which is what any responsible list manager should provide. Instead, the confirmation message simply includes this text:
If you have technical questions, please submit them to http://customersupport.kintera.org.
Visit that URL, and you'll see a "Customer Support Help Request Form." It's totally generic. There's nothing on the form about unsubscribing from mailings managed by Kintera.
I went ahead and used to form to ask how to remove myself from the CauseNet list. I soon recieved an email from Kintera confirming my request for information. The first line of the message stated, "PLEASE DO NOT REPLY TO THIS E-MAIL, AS IT CANNOT BE ANSWERED FROM THIS ADDRESS."
Maybe the folks at Kintera should read their own whitepaper about dealing with spam. The company's CTO gives this advice to people who send mass emails: "Include a prominent return email address and a convenient option to opt-out from receiving further emails."
I'll update this posting if and when I hear anything useful from Kintera about my unsubscribe request. In the meantime, I think it's pretty safe to say that the CauseNet list is poorly managed, and it's completely plausiible some Cuban-antagonist signed him up out of spite.
[UPDATE: Just 33 minutes after I sent my question via the Kintera web form, I got back a terse message stating:
The following has been updated for your Communication Preferences:Do not direct mail
Do not phone
Do not email
Not exactly "leading edge technology," but I guess it's the best Kintera can do. After all, they use the same system for their own Kintera Connect eNewsletter.]
Posted by Brian at 10:15 AM | Comments (3)
March 7, 2006
Mortgage spamming kit up for auction
Somebody is selling a mortgage spamming kit on eBay. (OK, he's actually calling it a Real-time mortgage lead Delivery and filter system.)
The seller, who says his name is Jason Pitts and claims to live in Tucson, Arizona, wants no less than $6,000 for some website forms and a database of thousands of "mortgage lead buyers," and a similar amount of "recent mortgage leads." (I especially like the little "We are compliant with CAN-SPAM" graphic that comes with the package.)
The auction appears to be some kind of going-out-of business fire sale, maybe because Pitts got listed on the Spamhaus Register of Known Spam Operations.
Pitts, who also goes by the handle J_Data, announced the auction on the SpecialHam.com spammers forum last month and apparently didn't get any takers.
Get it while it lasts.
Posted by Brian at 11:40 PM | Comments (5)
Porn spammer ran a support site for moms
 Talk about diversifying your online portfolio. A "fetish porn" spammer who faces jail time is also the operator of a site for work-at-home moms (WAHMs).
Talk about diversifying your online portfolio. A "fetish porn" spammer who faces jail time is also the operator of a site for work-at-home moms (WAHMs).
Jennifer Clason, 33, of Raymond, New Hampshire, just pleaded guilty to violating CAN-SPAM and criminal conspiracy. As part of the plea, entered in federal court in Phoenix, Arizona on Monday, she has agreed to forfeit the profits from her crimes. She also faces up to five years in prison for each of the offenses, which included "the transmission of numerous spam e-mails containing graphic pornographic images."
If Clason goes to jail, it's going to cut into her time as operator of a site called MommyJobs.com -- a self-proclaimed "support site" for work-at-home moms looking to make some money. Sounds pretty wholesome, but MommyJobs.com isn't completely innocent. Check out the site's message board, where there are rousing discussions of get-rich schemes, including "get paid to read email" (PTR) and "auto surf" programs and HYIP (high-yield investment program) scams.
 No evidence on the boards that Clason attempted to convince the WAHMs to sign up for Phatbucks.com, her affiliate program for porn spammers, or to visit her porn" thumbnail" site, or her porno webmaster content site.
No evidence on the boards that Clason attempted to convince the WAHMs to sign up for Phatbucks.com, her affiliate program for porn spammers, or to visit her porn" thumbnail" site, or her porno webmaster content site.
Clason, who sometimes did business as Coast to Coast Cash, landed on the ROKSO list (not to mention in the cross hairs of the Department of Justice) for using spam to promote her porn biz. Her partners in porn spam included Jeffrey A. Kilbride of California and James R. Schaffer of Arizona.
But Clason seemed to avoid that type of promotion for MommyJobs.com. In fact, she did an amazing job of getting how-to articles placed in publications, with the goal of gaining publicity for MommyJobs.com. Just last month, she had a piece about Google ads published at DailyIndia.com.
 Clason is scheduled to be sentenced June 5. In the mean time, she continues to post messages at MommyJobs.com, where members appear to be oblivious about their moderator's legal issues. Last Friday, Clason announced she was heading to Phoenix "to tend to some business." A board member replied, "Jen's finally gonna have a vacation!!!"
Clason is scheduled to be sentenced June 5. In the mean time, she continues to post messages at MommyJobs.com, where members appear to be oblivious about their moderator's legal issues. Last Friday, Clason announced she was heading to Phoenix "to tend to some business." A board member replied, "Jen's finally gonna have a vacation!!!"
Posted by Brian at 8:06 PM | Comments (8)
March 6, 2006
Spam announces new anti-spam service
![]() Here's one from the what-were-they-thinking department: a new anti-spam service called Spam Strike announced its launch over the weekend by spamming would-be subscribers.
Here's one from the what-were-they-thinking department: a new anti-spam service called Spam Strike announced its launch over the weekend by spamming would-be subscribers.
The spams (sample here) state that Spam Strike harvested the recipient's email address from a web page. According to the messages, "This technique is a common way for spammers to obtain your e-mail address and we strongly recommend you take steps to have your data removed or concealed."
The spams, sent from a Tiscali DSL connection in the UK, go on to invite recipients to sign up for the Spam Strike service ($15.99/year) and receive regular reports about the vulnerability of their email contact information.
According to a FAQ at the Spam Strike site, the service "scans online databases looking for personal information that spammers would use and then warns as many users as possible who have had their private details made publicly available, often without their knowledge or consent."
Reaction to the new service was swift and negative. Spamhaus director Steve Linford weighed in to the discussion on the Nanae newsgroup, warning that his group will blacklist the SpamStrike.net site if its promotion spams hit any of the Spamhaus spam traps. Others have observed that SpamStrike smacks of a protection racket.
Spam Strike argues that they're not really spamming: they only send the warning ad once to a user; they make no effort to conceal their identity; and they offer an ethical service.
All of those claims are as yet untested. Spam Strike's operators appear to be in the UK, but there's nothing at the site or in its whois record to reveal the names or other details about who's behind the service. Besides, there's the issue of the legality of conducting automated scans.
To their credit, a Spam Strike representative made an appearance on the Nanae newsgroup to respond to the criticism of its spammed "warnings." The anonymous rep wisely announced that SpamSrike won't be sending any more spam. "We've decided to engage potential customers through traditional advertising channels, although some of us feel that by not issuing the warnings, we are hanging a lot of people 'out to dry.'"
The mysterious folks behind SpamStrike.net are not the first to launch an anti-spam service using that name. (Information on other Spam Strike offerings is here and here. But hopefully they'll be the last to try marketing such a sketchy service in such a boneheaded manner.
Posted by Brian at 10:38 AM | Comments (1)
March 3, 2006
Leeching off Begg-Smith
Two new articles out of Australia about Olympic medalist Dale-Begg Smith and spyware: Spyware cybersigns point to Begg-Smith and Spyware critics question mogul Begg-Smith's rise.
Both articles include quotes from Andrew Forin, defending Begg-Smith. Forin, who identifies himself as a childhood friend of Begg-Smith's, sent me some emails last month in response to my blogging about Begg-Smith and spyware. 
"Are you leeching off of Dales publicity?" asked one of Forin's messages.
I thought it was an odd thing for him to ask, given that his initial email to me promoted a book he's apparently writing about Begg-Smith. Forin wants people to pay $25.00 for the e-book, even though it's not even published yet. Here's how the budding author described his project (typos and spelling/grammar problems intact):
"One in Forever" Is the story of my life with Dale from the time I first met him in grade 11 up until Feb 15 2006. It give's an introspective view of Dales Character throughout the book, and even though I would never be able to re write the stories of what happened in our lives as unreal as they actually were, im sure anybody would still be quite satisfied with how unbeliveable, hilarious, emotional, horrifying, mind blowing, and incomprehendible our lives were when we were around each other.
Forin has himself dabbled in spam -- and a really low-grade version to boot. Two years ago, he sent out several batches of chain-letter spams (examples here and here). Similar spam-scams have drawn lawsuits from the US Federal Trade Commission. According to the FTC, "If you start a chain email or letter or send one on, you are breaking the law."
When I asked him, Forin didn't deny sending the chain-letter spams. "I guess you can just post whatever you want on your own site," he said.
What's more, Forin is a pop-up spammer, just like his old buddy. In 2004, Forin sent out spams advertising his site, AdVolume.com. In the messages, Forin sough to purchase "US pop up/under or banner traffic."
Note to reporters: Forin may not be the best source to use as a judge of Begg-Smith's character.
[Update: Judging from member remarks at one webmaster forum where Forin posted ads for his pop ups in 2004, Forin was quickly sniffed out as a spammer.]
Posted by Brian at 1:38 PM | Comments (5)
March 1, 2006
Stock spammers stung by Secret Service
I've held off on blogging about the reported arrest last week of spammers Adam Vitale (booking photo below) and Todd Moeller until I could get more facts about the case. I've now got some of the details, thanks to a previously sealed deposition of a U.S. Secret Service agent, which includes some juicy excerpts of instant-message conversations involving the two men. 
Vitale and Moeller, part of a spam operation known as g00dfellas, have struck me over the years as low-level, blustering spammers, often accused of ripping off their partners -- in other words, they're hardly "spam kings" as others have called them.
But their arrest is still significant. While Moeller (aka trill) and Vitale (aka Batch1 and n1hustler4life) have sent spam for everything from pills to college diplomas, their big money-maker of late has been stock spams -- one of the most vexing types of spam out there right now.
According to the February 17 complaint, Moeller boasted to a fellow spammer (working for the feds as a confidential informant or CI) that he and Vitale were making $40,000 per week sending spam that touted shares of small-cap stocks -- a practice known as pump-and-dump spamming. The two operated a company called Viatelecom aka Via Telecom LLC to do their stock deals.
In an April, 2005 instant message conversation with the CI, Moeller claimed that he had 40 servers for sending spam, as well as 35,000 "peas" or proxies to disguise the true origin of the spams. He said he exclusively spammed AOL members and boasted he could send millions of spams per hour, with less than 20 percent getting caught in AOL's spam filters.
In July of last year, Vitale contacted the CI and offered to hire him as a "mailer" for stocks. According to court documents, Vitale offered to pay the CI $10,000 if he could "make it move" (increase the stock's sales volume).
But it was anti-spyware software spamming that tripped up the two spammers. It all started in April, 2005, when the CI contacted Moeller to try to hire him to send spam for what the feds called "a "purported computer security product" (later referred to as an anti-spyware program).
After months of wrangling over fees and payments, Moeller finally agreed in August to spam for the CI if he was made a full partner, receiving 50% of proceeds. To get the ball rolling, the CI (actually, it was law enforcement agents) wired $1,500 to Moeller in New Jersey. Soon, Moeller began hammering AOL with spams for the anti-spyware product.
At one point, Moeller boasted that his proxies included AOL systems, which enabled him to "proxy lock the [aol] domain and use the internal smtp." However, AOL has told the Secret Service that "most, if not all" of the spams from Moeller/Vitale were sent using Internet IPs and not from AOL's internal network.
Toward the end of August, Vitale contacted the CI, angry that he was paying Moeller, not him. Vitale claimed he was the one doing the mailing, and that Moeller just created fake email headers. "You don't get it do you dum [expletive deleted]?" said Vitale.
Judging from an assortment of online complaints, Vitale has been involved in numerous cases of partners double-crossing each other.
According to the Secret Service, before the sting was over, AOL's filters had registered a total of 1,277,401 spams from Moeller and Vitale. A review of a small portion of the spams showed they had been sent from 73 unique IP addresses (aka proxies).
In spammer forums, there's speculation that the CI was Sean Dunaway, whom you may recall was the Nevada man busted in 2004 for co-conspiring to steal AOL's member database and sell it to other spammers. According to the court docket, Dunaway pled not guilty to defrauding the US in January 2005 and his case is still open.
But spammers have told me that the informant was a spammer who used the online nickname m3rk and who resided in Boca Raton. Perhaps that's Sean Brooks, who identified himself in this online resume as being 22 years old and "extremely good with coding America Online Applications."
No word yet on other members of the g00dfellas gang, who went by aliases including Orlando. But the arrests have certainly shaken up some spammers. When I greeted one spammer online the other night, his first comment was, "skared ... goodfellas went down."
Posted by Brian at 2:04 PM | Comments (9)
